CVE-2020-0796 Introduction
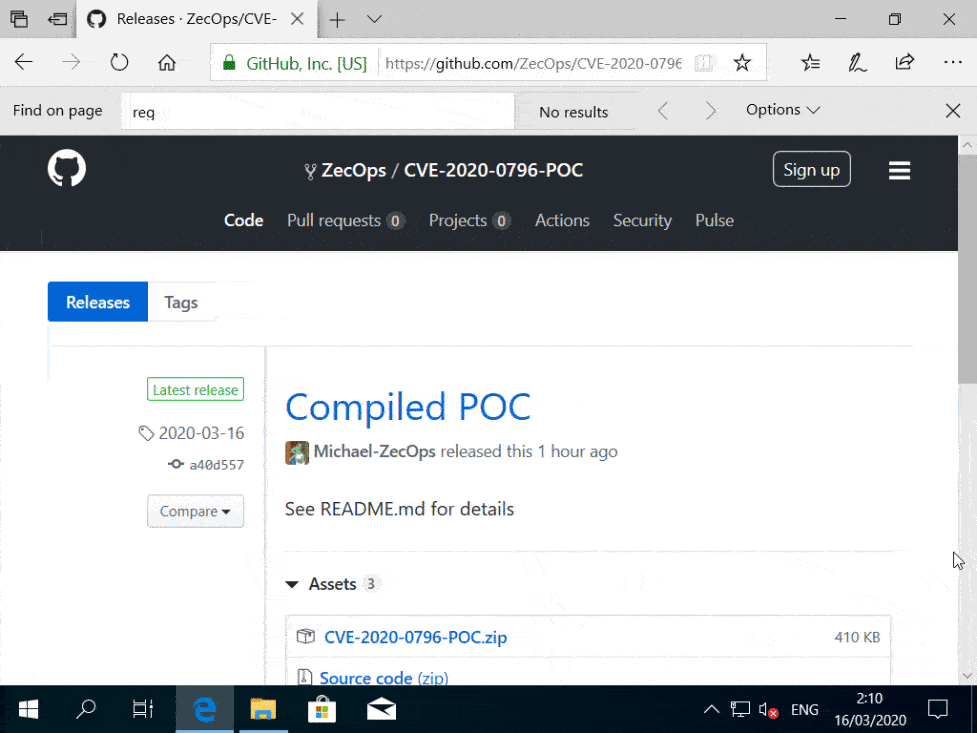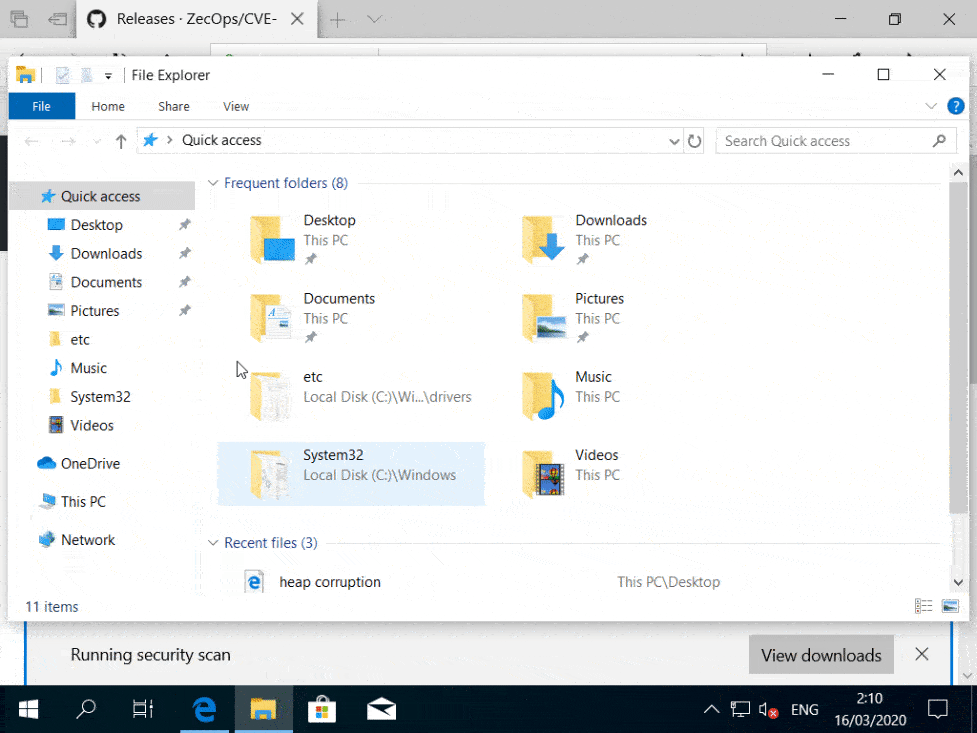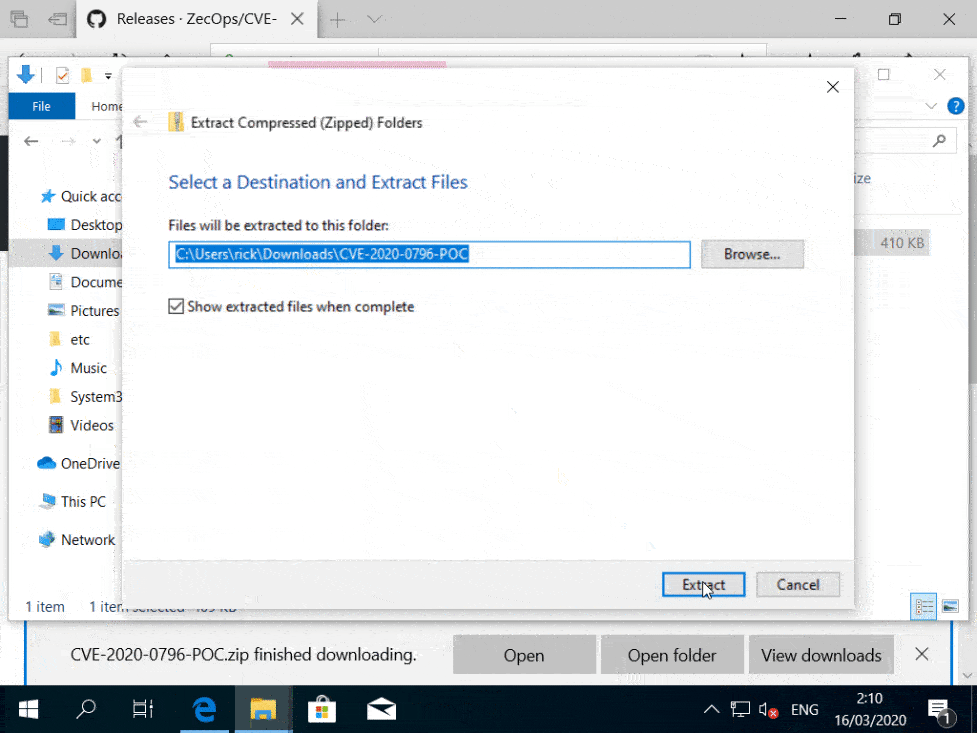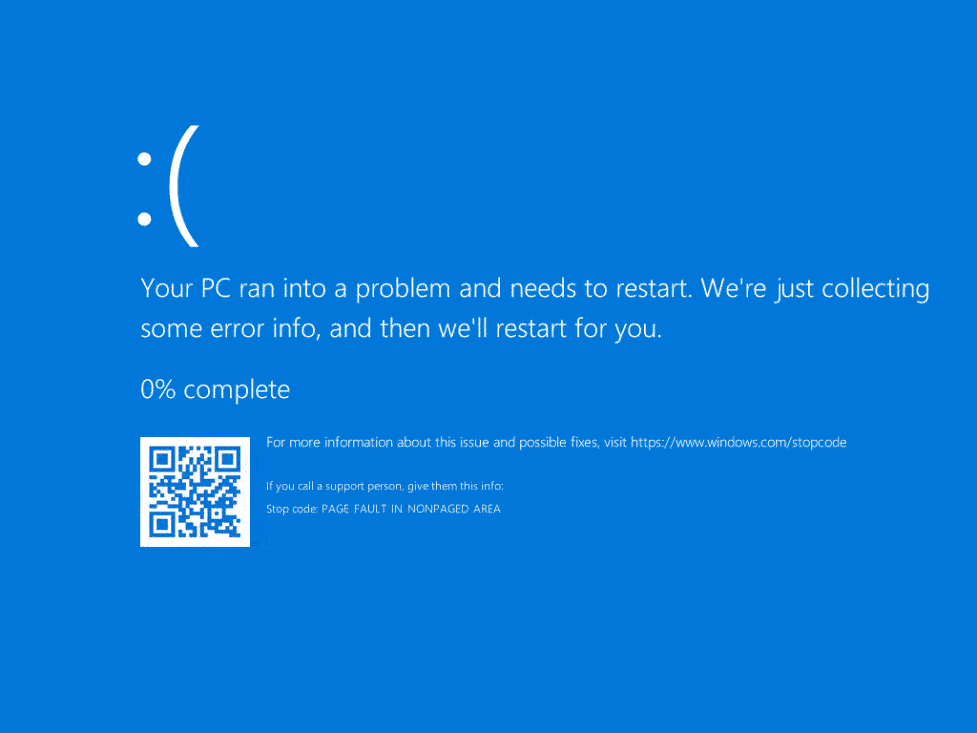
Microsoft recently announced a bug in the compression mechanism of SMBv3.1.1. The bug is also known as “SMBGhost”. This bug has serious implications in managed networks. Windows 10 versions 1903 and 1909 are affected.
Lucas Georges shared an excellent write-up. Even though the full code wasn’t shared, the details were sufficient for a quick implementation.
In Lucas’ proof of concept, the vulnerability required username and password for the target machine, however we were able to implement a version that doesn’t require credentials by triggering the bug in an earlier stage. Following our implementation, we noticed that there’s another publicly available proof of concept code in Python with a similar technique.
Proof of Concept
This POC is released for Research and Academic purposes only. Use at your own risk.
POC source code (C#) is available at: https://github.com/ZecOps/CVE-2020-0796-POC.
Pre-compiled POC is available here: https://github.com/ZecOps/CVE-2020-0796-POC/releases/tag/2020-03-16
Usage: CVE-2020-0796-POC.exe [IP]
Example: CVE-2020-0796-POC.exe 192.168.1.5
Note: If [IP] is not provided, the POC will run on localhost (127.0.0.1)
Impact: This is a serious vulnerability that can be used to cause existing threat operators to spread laterally. Similar issues caused “NotPetya” and “WannaCry” ransomware. We recommend to treat this vulnerability seriously.
Remediation
- We recommend updating servers and endpoints to the latest
Windows version to remediate this vulnerability. If possible, block port
445 until updates are deployed. Regardless of CVE-2020-0796, we
recommend enabling host-isolation where possible.
- It is possible to disable SMBv3.1.1 compression in order to avoid triggers to this bug, however we recommend to do full update instead if possible.
ZecOps Customers & Partners
ZecOps Digital Forensics and Incident Response (DFIR) customers can detect such exploitation attempts as “CVE-2020-0796” using ZecOps agentless solution: Neutrino for Servers and Endpoints. To try ZecOps technology and see a demo, you can contact us here.
Stay safe,
ZecOps Research Team.